At the end of the day yesterday, I'd resolved the connectivity issue between our Jamf Pro server and our Jamf Infrastructure Manager server. I'd also managed to get it to do an LDAPS lookup with my own account, but not the service account. Today, that was resolved... The service is working.
We've had Jamf Pro in place for some time but haven't really done anything with users as all content was being assigned to devices (as is right and proper). However, a recent issue came up where I needed to assign something by user and accelerate the implementation of the LDAPS connection.
Here's an overview of how it's all supposed to connect:
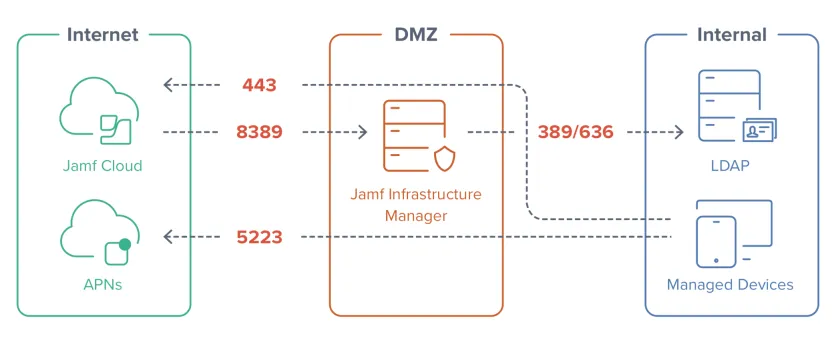
The JIM (Jamf Infrastructure Manager) server was in place and reporting the LDAP Proxy service as available in Jamf Pro but no matter what I tried, it just wouldn't connect. I made sure all of the relevant ports were open on the DMZ and the JIM firewall to accept requests from the Jamf Pro IP address - nothing. Running netstat showed that the server wasn't even listening on the expected port even though the setup and installation reported no issues.
A bit of back and forth between me and our Jamf contact led me to finding the relevant logs showing that it was having issues binding the port to itself for listening - a breakthrough moment.
The quickest solution for this was to make a change in the hosts file to resolve its FQDN (jim.domain.com) back to the internal IP address (192.168.1.1). After this, restart the Jamf Infrastructure Manager service and it starts listening... finally!
Back over to Jamf Pro and it's confirmed, it's now giving me another error that the username and password required for authentication isn't working. I tried many different combinations of formatting for the username until finally attempting it with an account that had far more permissions than this account should need - it worked and the test lookup returned results. After trawling through the atributes and group memberships in AD to find the difference , I narrowed it down to a security group that allowed connectivity to the DMZ server in question which in turn allowed the LDAP proxy to talk to AD. With a proper service account setup, lowest permissions required and lookups working, the job was FINALLY done.
This was a challenge that truly made me want to give up so I'm writing it here in the hope that I never forget what I had to do in the event that I ever need to set up a Jamf/JIM/LDAP Proxy service again.
I wish I'd found this post from Travelling Tech Guys blog before, because it pretty much explains most of what I went through and would have saved so much time.
I hope this short rant and link to Travelling Tech Guy helps someone else.
